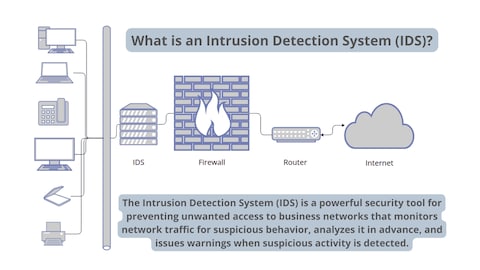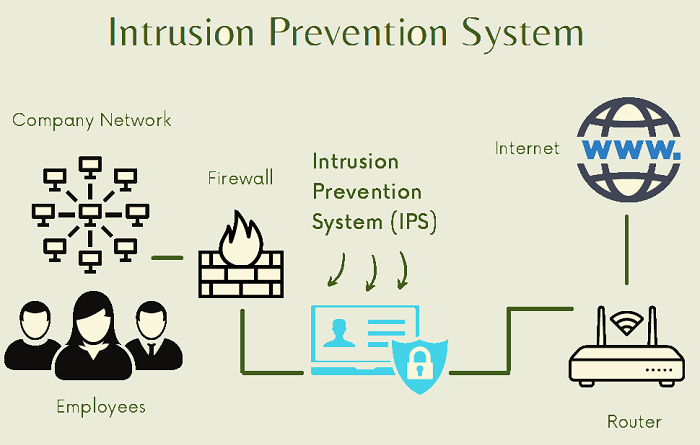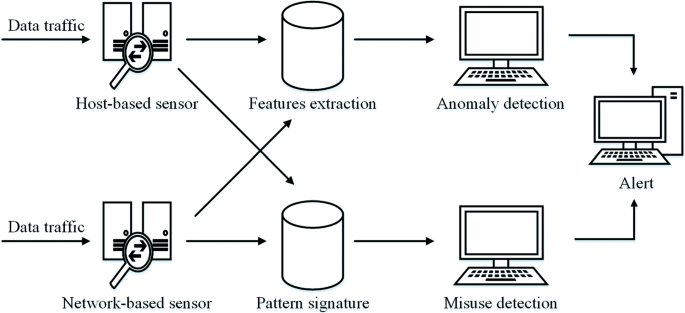
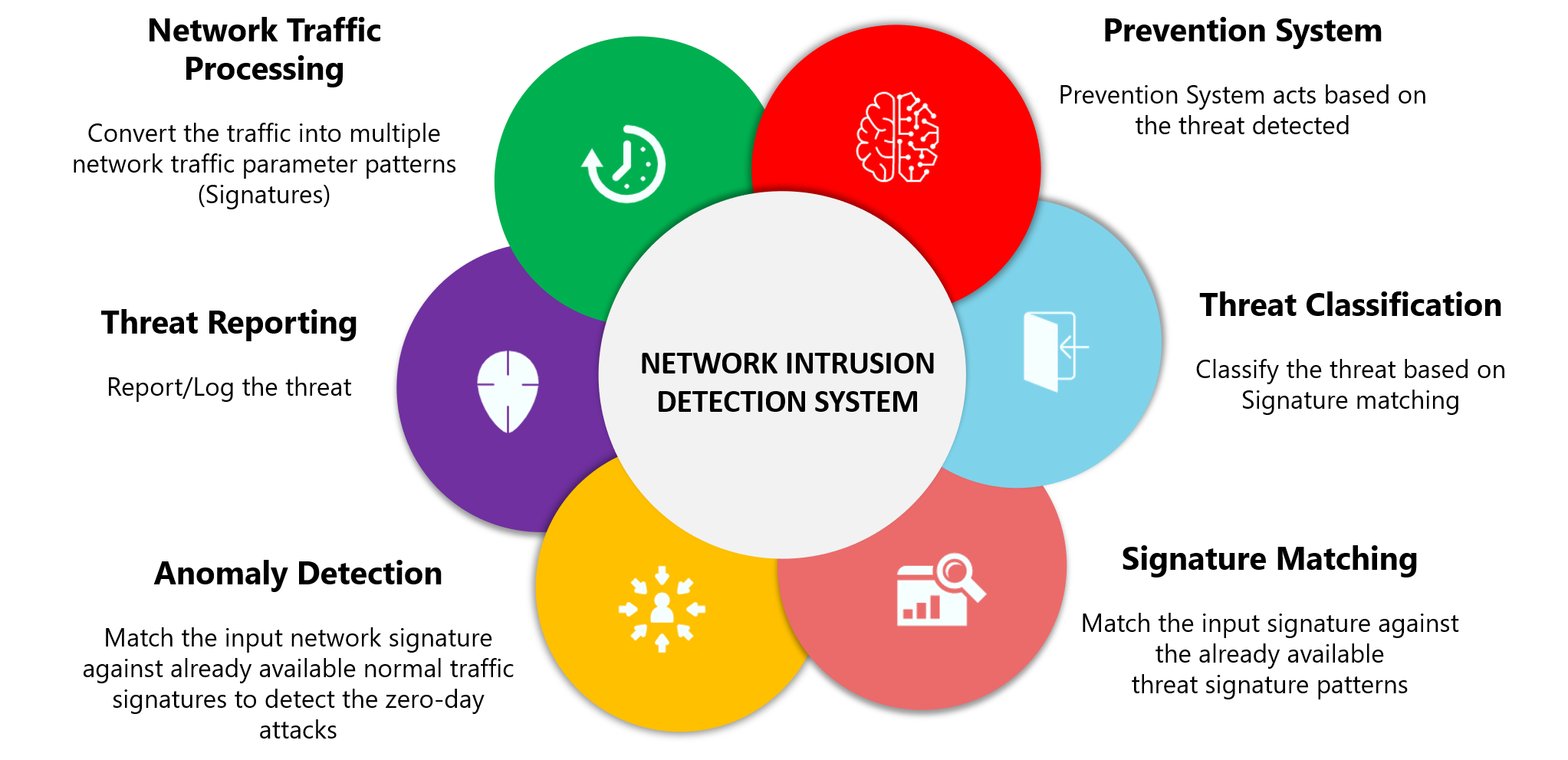
Intrusion detection systems for IoT-based smart environments: a survey | Journal of Cloud Computing | Full Text
Securing the Internet of Things with Intrusion Detection Systems - BPI - The destination for everything process related
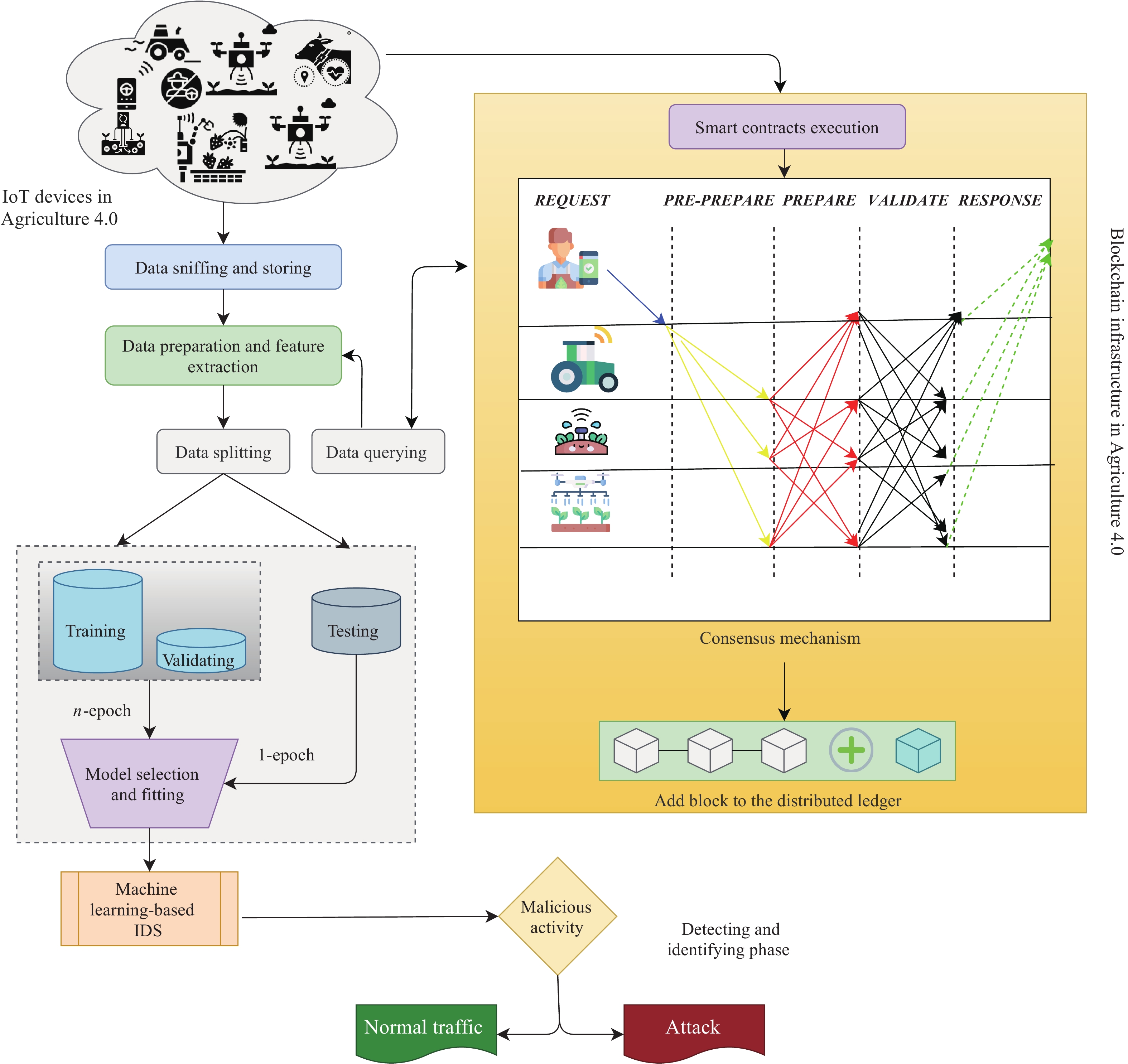
Cyber Security Intrusion Detection for Agriculture 4.0: Machine Learning-Based Solutions, Datasets, and Future Directions

An Exhaustive Research on the Application of Intrusion Detection Technology in Computer Network Security in Sensor Networks

An improved malicious code intrusion detection method based on target tree for space information network - Chundong She, Yaqi Ma, Jingchao Wang, Luting Jia, 2017
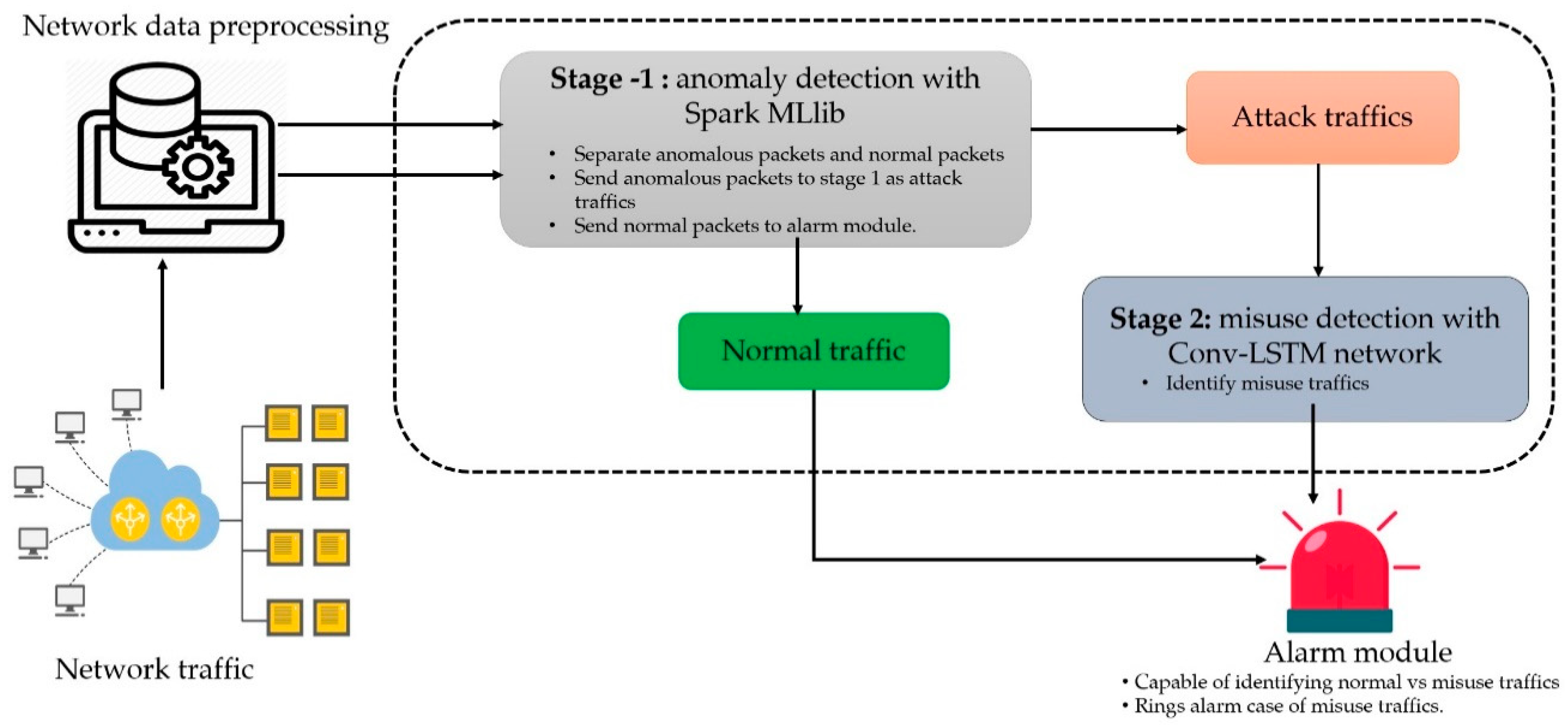
Symmetry | Free Full-Text | A Scalable and Hybrid Intrusion Detection System Based on the Convolutional-LSTM Network
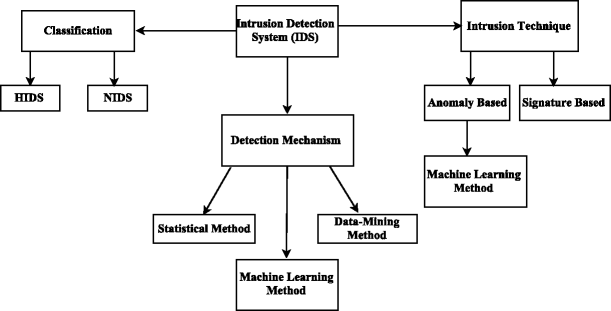
Survey on SDN based network intrusion detection system using machine learning approaches | SpringerLink
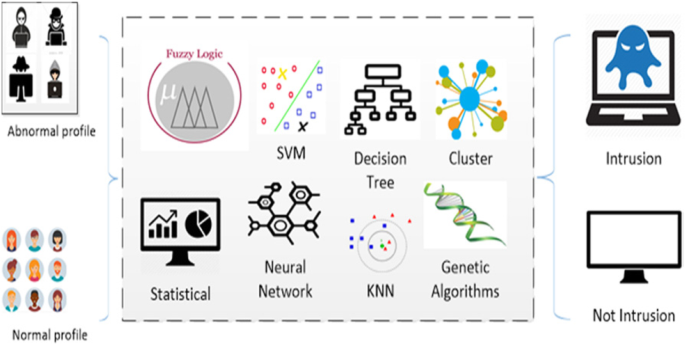
Survey of intrusion detection systems: techniques, datasets and challenges | Cybersecurity | Full Text
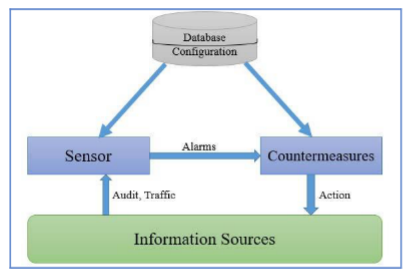

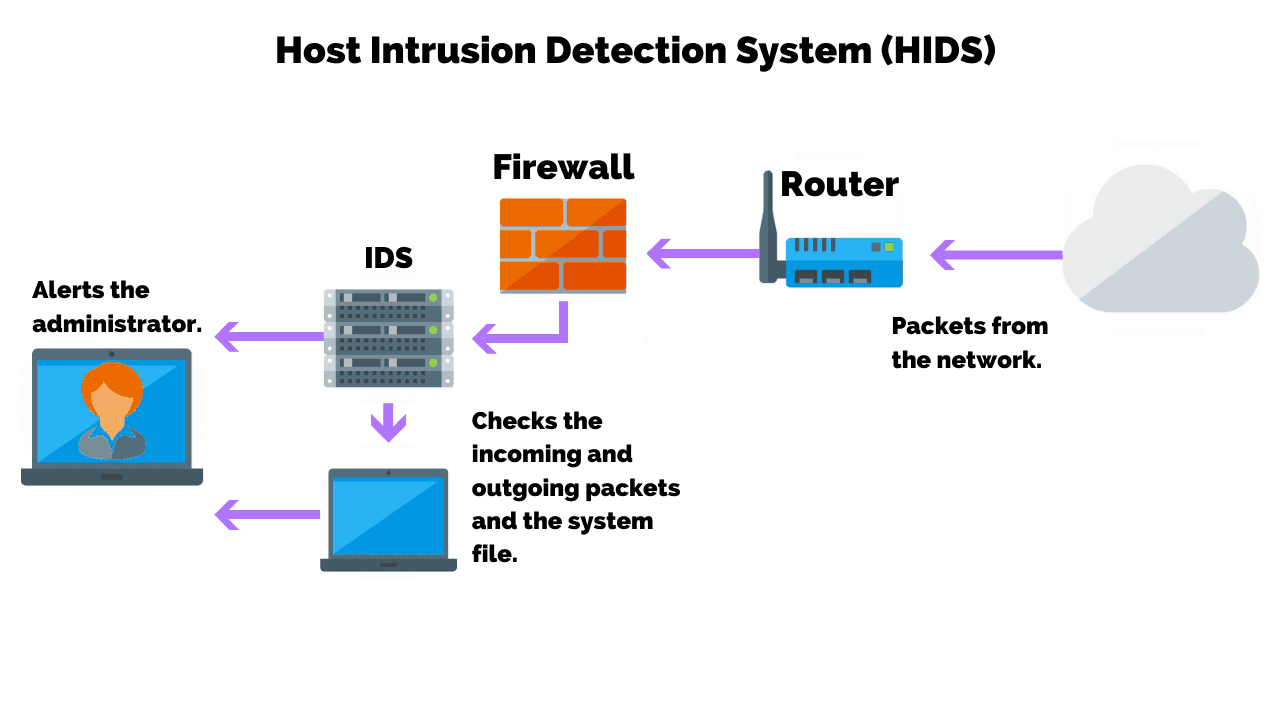


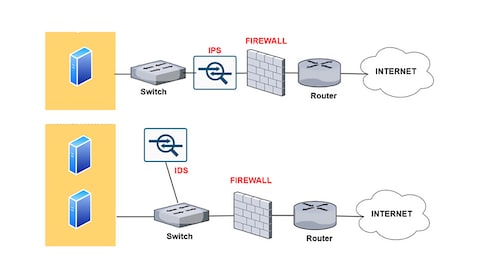
![Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ] Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-820/1/fig-1-2x.jpg)